top of page
搜尋


IOT Hardware Firewall
As you can see , we using ID4 photo as an example to demonstrate how important it is to have security protection to defend hackers. In...
Steven Chang
2025年6月24日讀畢需時 4 分鐘

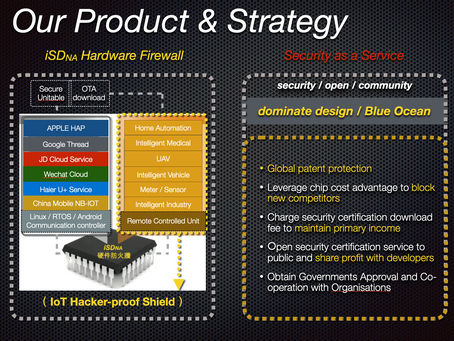
iSDNA IOT Product and Strategy
iSDNA IOT Product and Strategy
Steven Chang
2025年6月24日讀畢需時 3 分鐘


Case Study for Android & mPOS security
This slide is to show android is very insecure; it endangers traditional POS transaction. Originally, traditional POS has EMV / PCI...
Steven Chang
2025年6月24日讀畢需時 2 分鐘


iSDNA Advantage : Better then eSE / ARM TrustZone ..
iSDNA Advantage The current security protection mechanisms for IoT and the entire internet follow a common structure. Both the cloud ...
Steven Chang
2025年6月24日讀畢需時 3 分鐘

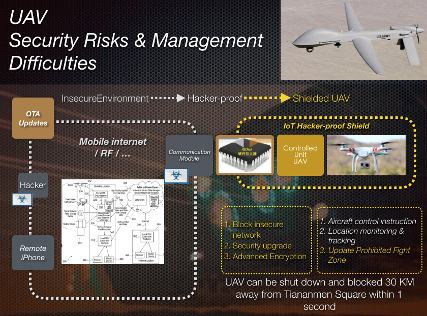
Case Study : UAV Security Management
Currently(2017), there are around 550,000 drones in the United States, and this number will only continue to grow worldwide. The vast...
Steven Chang
2025年6月24日讀畢需時 3 分鐘


Case Study : Smart Vehicle Safety Control
Last month, China's Tencent Keen Security Lab exploited a security vulnerability in Tesla's Android system, successfully gaining remote...
Steven Chang
2025年6月24日讀畢需時 2 分鐘
bottom of page